If your helpdesk handles sensitive data like medical records, financial details, or performance reviews, you may need to comply with Protected B standards in Canada. This classification safeguards data that, if compromised, could lead to serious harm, such as identity theft or financial loss. Here’s what you need to know:
- Protected B Data: Sensitive information requiring strict security measures.
- Data Residency: Protected B data must be stored and processed within Canada.
- Compliance Risks: Using non-compliant platforms can lead to legal issues, data breaches, and lost contracts.
- Helpdesk Requirements:
- Canadian-based data centers.
- Encryption with exclusive control over keys.
- Security-screened personnel.
- Audit logging and monitoring.
If you work with Canadian government entities or regulated industries, ensuring your helpdesk platform meets these standards is essential for legal and operational success.
How Protected B Affects Helpdesk Operations
When your helpdesk deals with Protected B data, you’re navigating a landscape filled with legal, technical, and operational challenges. These complexities have a direct impact on how your team functions and ensures compliance.
Compliance Risks for Support Teams
Handling Protected B information comes with high stakes. Privacy breaches involving this type of data must be reported to the Office of the Privacy Commissioner (OPC) and the Treasury Board of Canada Secretariat (TBS) within just 7 days.
One of the biggest risks stems from jurisdictional exposure. For instance, laws like the U.S. Foreign Intelligence Surveillance Act (FISA) allow U.S. agencies to compel service providers to hand over data – even without notifying your organization. The Government of Canada White Paper highlights this concern:
"The primary risk to data sovereignty is the US Foreign Intelligence Surveillance Act (FISA) and the US government’s ability to compel an organization subject to US law to turn over data under its control, regardless of the data’s location and without notifying Canada."
Even if your data is stored in Canada, it may not be safe if your service provider operates under foreign jurisdiction. For example, a U.S.-based company running data centers in Canada could still be subject to American legal demands. This legal exposure raises the stakes for helpdesk operations, as any mishandling of data could have serious consequences.
Non-compliance doesn’t just lead to legal trouble – it can disrupt operations. For organizations working with the Canadian government or other regulated sectors, failing to meet Protected B standards could disqualify them from critical projects. Beyond that, unauthorized disclosures – such as leaks of medical records, financial data, or performance evaluations – could harm individuals or organizations and erode public confidence.
On top of these risks, SaaS platforms’ data storage practices introduce additional hurdles for helpdesk teams.
Data Storage Issues with SaaS Helpdesk Platforms
Global SaaS platforms often clash with Protected B’s strict requirements for Canadian data residency. Many of these platforms transfer client data across borders to improve performance, which directly conflicts with the mandate to keep data within Canada.
Another challenge is that SaaS providers frequently retain access to customer data for tasks like technical support or maintenance. This access increases the risk of unauthorized disclosure, especially under foreign legal orders.
While cloud providers secure their infrastructure, it’s up to helpdesk teams to enforce data classification and control access. Unfortunately, many teams only realize their accountability during compliance audits, which can expose gaps in their processes.
As of 2018, at least five major cloud providers had the technical ability to keep data within Canada. However, their default configurations often don’t meet Protected B standards. To ensure compliance, organizations must adopt specialized packages – such as Google’s "Data Boundary for Canada Protected B" or Azure’s "Canada PBMM" policy sets. These tools help restrict data location and limit access to screened personnel. For helpdesk leaders, verifying these compliance features is a critical step before integrating SaaS solutions.
How to Determine If Your Helpdesk Needs Protected B Compliance
Figuring out if Protected B compliance is necessary starts with understanding your clients and the kind of data handled in your support tickets.
Questions to Ask About Your Compliance Needs
Begin by taking a close look at your client base and the type of support services you provide. Do you work with Canadian federal or provincial agencies that demand Protected B controls? The Government of Canada requires its departments to classify data and apply security measures, including Protected B, when using public cloud services. Similarly, organizations working with British Columbia’s government must adhere to data residency rules outlined in the Freedom of Information and Protection of Privacy Act (FOIPPA). Does your contract include specific security requirements? If you’re a private company offering B2B services to the federal government, compliance with the Contract Security Program is mandatory when handling Protected B data.
Next, assess the data in your support tickets. Items like medical records, financial documents, performance reviews, or proprietary contracts could trigger the need for Protected B compliance. Ask yourself: Would unauthorized access to this data result in financial loss, distress, or harm to reputations? If the answer is yes, compliance isn’t just a recommendation – it’s a requirement.
These questions can help identify where stricter security measures are needed. From there, consider industry-specific situations where Protected B compliance is essential.
Industries and Scenarios That Require Protected B
Certain industries face higher stakes when it comes to data protection. For example, healthcare organizations managing medical records, genetic data, or biometric details must meet Protected B standards to avoid risks like discrimination or severe personal distress. Financial services firms handling sensitive information such as bank statements, credit scores, or tax documents must guard against identity theft and financial fraud.
Government contractors have some of the strictest obligations. If your helpdesk supports federal Crown corporations or participates in service-sharing agreements, your contracts likely require compliance with Protected B standards. Data such as performance evaluations, criminal records, or details about racial or ethnic origins fall under Protected B because their exposure could lead to legal issues or human rights violations. If your helpdesk processes this kind of information, treating compliance as optional isn’t an option – it’s a business imperative.
What Helpdesk Systems Need for Protected B Compliance
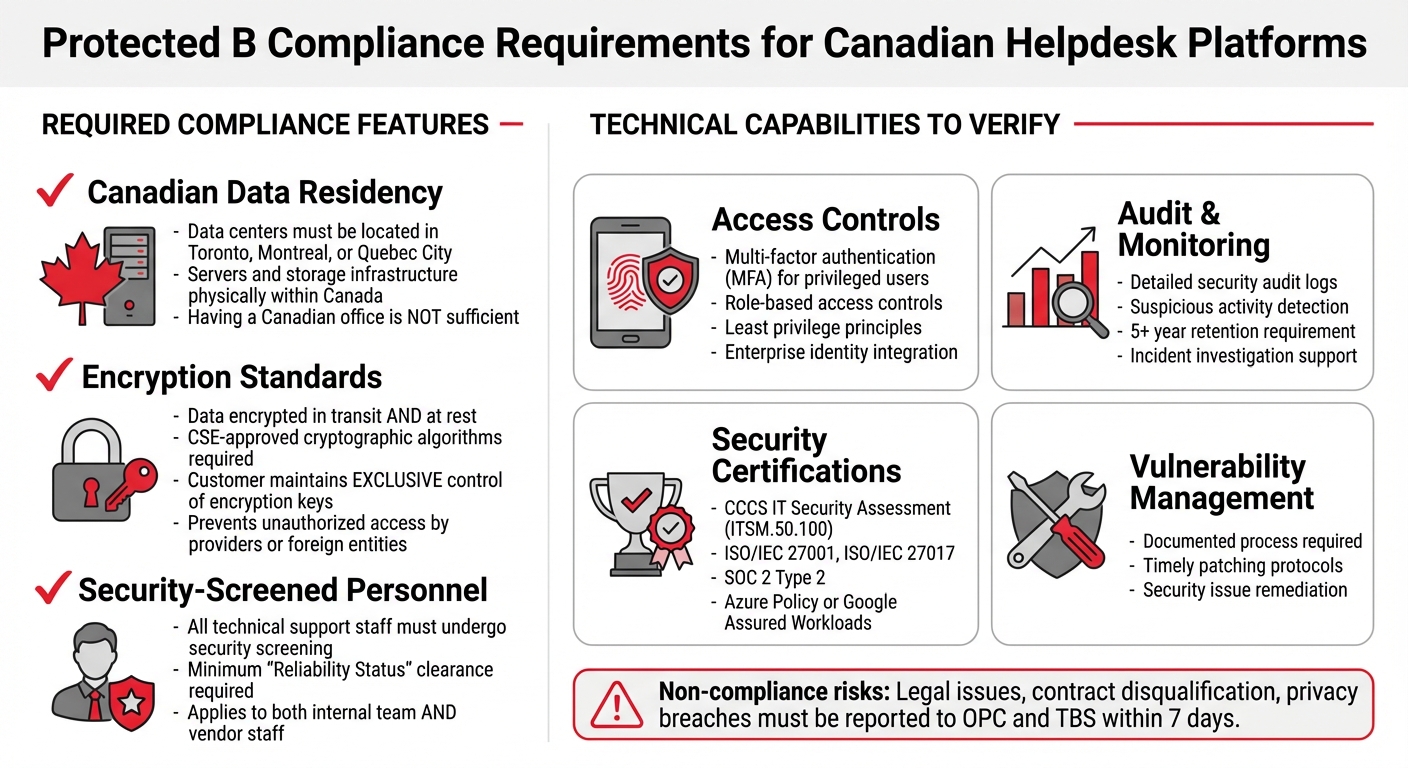
Protected B Compliance Requirements for Canadian Helpdesk Platforms
Once you’ve identified the need for Protected B compliance, the next step is understanding what your helpdesk platform must include to meet these requirements. Ensuring compliance means addressing both technical and operational aspects to protect against the risks previously outlined.
Required Compliance Features
Canadian data residency is non-negotiable. Your helpdesk platform must store and process all Protected B data within Canada. This requires dedicated data centers located in Canadian cities such as Toronto, Montreal, or Quebec City. Having an office in Canada isn’t enough – the actual servers and storage infrastructure must reside within the country.
Encryption must meet specific standards, with exclusive key control. Data must be encrypted both in transit and at rest using cryptographic algorithms approved by the Communications Security Establishment (CSE). Additionally, the Government of Canada mandates that customers maintain exclusive control of their encryption keys to prevent unauthorized access by service providers or foreign entities. As stated in the Government of Canada White Paper:
"The GC will be directing that: all protected data hosted in the cloud be appropriately encrypted while in transit and at rest [and] the GC maintain exclusive control of the encryption keys".
Security screening for personnel is required. Any technical support or administrative personnel with potential access to your data must undergo security screening, achieving at least "Reliability Status". This applies to both your internal team and the vendor’s staff. With these foundational elements in place, the next step is examining the platform’s technical controls.
Technical Capabilities to Verify
Beyond compliance features, your helpdesk platform must demonstrate strong technical safeguards. Start by ensuring multi-factor authentication (MFA) is enabled for privileged users. Role-based access controls should also be in place, adhering to the principles of least privilege and "need to know". Integration with enterprise identity services is essential to restrict sensitive data access to authorized personnel only.
Audit logging and monitoring are equally critical. Your helpdesk system must include detailed security audit logs to detect suspicious activity and support incident investigations. These logs must comply with government retention standards, which require keeping privacy breach records for at least five years. Without thorough audit trails, demonstrating compliance or responding to incidents effectively becomes nearly impossible.
Check for security assessments and certifications. Confirm that the platform has undergone the Canadian Centre for Cyber Security’s (CCCS) IT Security Assessment Process (ITSM.50.100). Independent audit reports, such as ISO/IEC 27001, ISO/IEC 27017, or SOC 2 Type 2, can further validate the provider’s security measures. Platforms offering automated policy tools – like Azure Policy or Google Assured Workloads – are particularly helpful in ensuring data remains within Canada and minimizing misconfigurations.
Finally, verify that the platform includes a documented vulnerability management process to ensure timely patching and remediation of security issues. These measures collectively build a foundation for Protected B compliance and operational security.
sbb-itb-e60d259
How to Assess Helpdesk Platforms for Data Residency
When evaluating a helpdesk platform for Protected B compliance, it’s essential to dig deeper than surface-level claims. Focus on verifying technical specifics, documentation, and operational practices that directly impact compliance. Here’s a breakdown of key questions to ask vendors and how to navigate the trade-offs involved.
Questions to Ask Platform Vendors
Start by confirming whether the platform has undergone the Canadian Centre for Cyber Security (CCCS) IT Security Assessment Process (ITSM.50.100). This assessment, based on the PBMM, establishes the baseline for Protected B compliance. Request access to the CCCS Summary Report or Technical Security Risk Assessment through the vendor’s compliance portal or designated compliance managers.
Next, ensure that the tools you plan to use are explicitly listed under the vendor’s “Services in Scope” for Protected B. A vendor’s agreement with the Government of Canada doesn’t automatically mean all features – like ticketing systems, databases, AI tools, or reporting modules – meet Protected B standards. Ask for clarification on which specific modules are covered.
Verify that the platform enforces a Canadian data boundary, with servers located in cities like Toronto, Montreal, or Quebec City. Additionally, check if the vendor allows your organization to maintain exclusive control over encryption keys for both data at rest and data in transit. This is an essential safeguard against unauthorized access.
Finally, confirm that the platform’s technical support team consists exclusively of personnel screened to "Reliability Status" or higher. Many global support teams don’t meet this standard, so ensure your contract guarantees access to Canadian-screened personnel.
Trade-offs and How to Address Them
While asking the right questions is vital, it’s equally important to weigh the trade-offs that come with Protected B compliance. For instance, restricting data storage to Canada might limit your vendor options since not all SaaS providers have local data centers. Similarly, requiring exclusive control of encryption keys can impact the functionality of features relying on real-time data processing or analysis. Smaller organizations may also find it challenging to manage encryption keys, access controls, and audit logs effectively.
Another consideration is cost. Enhanced security features like audit logging, multi-factor authentication, and personnel screening often come with higher price tags and may require enterprise-level agreements. However, some modern platforms offer solutions to offset these costs. Look for vendors that provide automated compliance tools, such as Google’s Assured Workloads or Microsoft’s Azure Policy for Canada PBMM, which streamline tasks like enforcing data residency and personnel screening.
To safeguard operational continuity, ensure the platform supports data export in vendor-neutral formats. This feature protects against risks like deplatforming and enables easier data recovery if needed. Additionally, many newer platforms built with security-by-default infrastructure can deliver Protected B compliance without the complexity or expense of traditional government-only cloud solutions.
Conclusion
Key Takeaways
For helpdesks managing sensitive information, adhering to Protected B compliance isn’t optional – it’s a critical responsibility. Key requirements include ensuring that data remains within Canada, retaining sole control over encryption keys, and employing support staff with at least a Reliability Status clearance. While cloud providers handle the security of their infrastructure, your organization is ultimately responsible for securing the data within that cloud. Failing to comply not only risks legal repercussions and contract cancellations but also jeopardizes customer trust and operational stability.
When evaluating vendors, don’t just take their word for it – dig deeper. Confirm that their platforms have passed established certification processes, such as the Canadian Centre for Cyber Security IT Security Assessment Process, to verify alignment with Protected B standards. Additionally, grasp the difference between data residency and data sovereignty. For instance, data stored in Canada by a U.S.-owned provider could still be subject to the U.S. CLOUD Act, which allows foreign authorities to demand access.
These insights provide a roadmap for immediate action.
Next Steps for Support Leaders
Now that the core requirements are clear, it’s time to take actionable steps toward compliance.
Start with a data audit to classify information based on sensitivity and pinpoint workflows that require Protected B-level controls. Review your vendor agreements closely to ensure they include clauses for disclosing unauthorized access, including cases involving foreign court orders.
Consider leveraging AI-powered platforms that not only meet Protected B standards but also enhance efficiency by 30–45%. Look for tools that can automate PII redaction using pattern-matching techniques, offer semi-autonomous options for human review in sensitive cases, and integrate seamlessly with existing security frameworks like Microsoft Purview to maintain role-based access controls. These features allow you to scale your support operations while staying compliant with Protected B requirements.
FAQs
What does Protected B data residency mean, and what are its requirements in Canada?
Protected B data residency involves the storage and management of highly sensitive information that demands advanced security measures. This classification, outlined by the Government of Canada, applies to data where a breach could result in serious harm to individuals, organizations, or government functions.
To comply with Protected B standards, cloud service providers must align with Canada’s security assessment framework. This framework evaluates several critical areas, including:
- Data ownership: Ensuring clear accountability for the data.
- Physical and personnel security: Implementing strict controls over who can access data and where it is stored.
- Operational practices: Following rigorous protocols for data handling and system management.
- Geographic location: Ensuring data remains within Canadian borders.
Providers must strictly follow these guidelines to achieve compliance, making this standard especially relevant for sectors like healthcare, finance, and public services that handle sensitive information.
What is Protected B data residency, and how can your helpdesk comply with it?
Protected B data residency involves storing and managing sensitive information within specific geographic boundaries to meet government security standards. This ensures that data remains secure and complies with strict regulations.
To meet these requirements, your helpdesk should prioritize cloud services designed for Protected B compliance. Options like sovereign or private clouds are ideal, as they ensure data storage and processing are restricted to approved locations.
Key Practices for Compliance
- Strict Access Controls: Limit who can access sensitive data to reduce risks.
- Encryption: Secure data both in transit and at rest to prevent unauthorized access.
- Physical Security Measures: Safeguard data centers to protect against breaches.
Additionally, partnering with cloud providers that meet Protected B standards and undergo regular compliance audits can help reinforce security. By aligning your helpdesk’s data residency strategy with these practices, you can safeguard sensitive information and adhere to regulatory requirements.
What are the consequences of not complying with Protected B data residency requirements?
Failing to meet Protected B data residency requirements can bring serious challenges. These include potential legal penalties, regulatory fines, and a damaged reputation with customers and stakeholders. Beyond that, non-compliance could open the door to unauthorized data access, exposure to foreign laws, or even data breaches.
For businesses managing sensitive information, such risks can be devastating. They might disrupt operations, tarnish your brand, and lead to expensive recovery efforts. Staying compliant isn’t just a legal box to check – it’s essential for safeguarding your data, maintaining customer trust, and steering clear of costly setbacks.