Switching to a non-US SaaS helpdesk requires Canadian teams to focus on three main areas: legal compliance, data residency, and vendor security. Here’s what you need to know:
- Legal Compliance: Ensure the provider aligns with Canada’s PIPEDA and provincial privacy laws. This includes securing contracts that guarantee comparable data protection and updating privacy notices to inform customers about foreign data processing risks.
- Data Residency: Understand where your data will be stored and processed. Data stored outside Canada may be subject to foreign laws, such as the US CLOUD Act, even if the provider isn’t US-based.
- Vendor Security: Verify the provider’s security certifications, breach response processes, and audit rights. Contracts should include clauses for data protection, usage limits, and breach notification timelines.
Key considerations:
- Public sector organizations often face stricter data storage rules, requiring data to remain in Canada.
- For sensitive data (e.g., health or financial information), assess the legal and political conditions of the provider’s jurisdiction.
- Conduct privacy impact assessments and pilot tests to identify risks before full migration.
Meeting Canadian Privacy Law Requirements
PIPEDA Compliance Requirements
Under PIPEDA, your organization is legally responsible for protecting personal information, even when transferring it to a non-US SaaS provider. The Office of the Privacy Commissioner of Canada clearly states:
"An organization is responsible for personal information in its possession or custody, including information that has been transferred to a third party for processing. The organization shall use contractual or other means to provide a comparable level of protection while the information is being processed by a third party."
To meet these requirements, ensure you establish secure, binding agreements with your providers. These contracts should include clauses that limit how vendors can use the data, enforce documented security protocols, and permit audits to verify compliance.
Additionally, update your privacy notices to inform customers that their data may be processed in foreign countries and could be subject to those nations’ laws. The Office of the Privacy Commissioner advises:
"Organizations need to make it plain to individuals that their information may be processed in a foreign country and that it may be accessible to law enforcement and national security authorities of that jurisdiction."
Conduct a detailed risk assessment by analyzing the sensitivity of your data and evaluating the legal, economic, and political conditions of the provider’s jurisdiction. Keep in mind:
"No contract can override the criminal, national security or any other laws of the country to which the information has been transferred."
Finally, review provincial rules to ensure your compliance efforts cover all applicable regulations.
Provincial Privacy Regulations
In addition to federal requirements, provincial laws add another layer of complexity. For example, in British Columbia, public sector organizations must complete a Privacy Impact Assessment (PIA) if sensitive personal data is stored outside Canada. Private organizations under BC’s PIPA are also responsible for ensuring that third-party providers uphold comparable protections.
Quebec’s privacy laws may involve unique considerations, such as language requirements and explicit consent mechanisms. If your organization operates in multiple provinces, you’ll need to confirm compliance with each region’s specific regulations, as some provincial laws impose stricter standards than PIPEDA.
Industry-Specific Privacy Rules
On top of federal and provincial requirements, certain industries have their own privacy rules. Financial institutions, for example, must adhere to OSFI guidelines when outsourcing data. These rules require careful evaluation of foreign legal and economic conditions.
Healthcare organizations face even stricter requirements in provinces like Ontario, New Brunswick, Nova Scotia, and Newfoundland and Labrador. Provincial health information laws often go beyond PIPEDA, demanding specific data residency measures for personal health information. If your organization handles sensitive health data, ensure that any non-US SaaS provider complies with the relevant provincial health privacy laws before proceeding.
Understanding Data Storage and Cross-Border Rules
Where Your Data Can Be Stored
Under PIPEDA, there’s no requirement to store data within Canada. Instead, the focus is on accountability – your organization is responsible for protecting the data, no matter where it’s stored.
However, public sector organizations like government agencies, schools, and hospitals must store their data in Canada due to regulations like FIPPA, PIIDPA, and PHIPAA.
Certain types of data have stricter rules:
- Tax records must remain accessible within Canada, as required by the Income Tax Act and Excise Tax Act.
- Defense-related data must be stored domestically under the Controlled Goods Program.
Another critical consideration is the jurisdiction of your data storage provider. If the provider is a U.S.-owned company, it will still be subject to the CLOUD Act, even if its servers are located outside the U.S.. This highlights the importance of evaluating the provider’s legal obligations alongside your compliance efforts to manage risks throughout the data lifecycle.
These storage rules directly influence how data can be transferred across borders.
Rules for Moving Data Across Borders
When transferring data internationally, PIPEDA treats such actions as a "use" rather than a "disclosure." This means you remain accountable for the data and don’t need additional consent if the transfer aligns with its original purpose.
To protect data during cross-border transfers, include safeguards in your contracts. These should cover:
- Audit rights
- Clear security measures
- Limits on how the data can be used
- Procedures for returning or disposing of data
Keep in mind, though, that no contract can override the laws of the country where the data is processed.
For sensitive information – like health records, financial details, or biometric data – evaluate both the sensitivity of the data and the legal, economic, and political environment of the destination country before proceeding. To reduce risks, use technical safeguards such as encryption with managed keys, role-based access controls, and detailed activity logs to monitor usage.
With these storage and transfer rules in mind, the next step is ensuring that your vendors meet security and reliability standards during the data migration process.
PIPEDA: Your Guide to Data Privacy in Canada
sbb-itb-e60d259
Checking Vendor Security and Reliability
Once you’ve completed compliance and data residency assessments, the next step is to evaluate vendor security, integration capabilities, and support agreements.
Security Certifications and Standards
Under PIPEDA, your organization is still responsible for protecting customer data, even when working with third-party vendors. That means you need to confirm that your vendor enforces strict security measures, complies with recognized standards, and allows audits to verify compliance.
"The organization shall use contractual or other means to provide a comparable level of protection while the information is being processed by a third party." – Principle 1, Schedule 1 of PIPEDA
Contracts should include clauses that secure your right to audit the vendor and ensure they adhere to high security standards. This way, you’ll have the tools to verify how personal information is handled and stored. Additionally, check that the vendor provides privacy training for their staff and implements effective security practices.
In case of a breach, the vendor’s response process must include immediate notification and detailed reporting. This should cover encryption status, the data accessed, and how long the exposure lasted. PIPEDA requires organizations to report breaches that pose a "real risk of significant harm" to the Privacy Commissioner and affected individuals. Your vendor must notify you promptly so you can assess the situation yourself. For instance, the Office of the Privacy Commissioner of Canada reviewed CIBC Visa’s outsourcing practices and found them compliant because the bank monitored legal requirements in the foreign jurisdiction and ensured the provider could maintain services under external pressures.
"An organization remains responsible for the personal information it has transferred to a third party for processing." – Office of the Privacy Commissioner of Canada
Vendors are also required to maintain records of all security incidents for at least two years, regardless of their severity. Be sure to include clauses in your contract that require secure disposal or return of your data when the agreement ends.
These rigorous security measures lay the groundwork for smooth integration with your systems, which is the next critical step.
Integration with Existing Tools and Workflows
Before adopting a new helpdesk, conduct a privacy impact assessment to identify any risks to data integrity during integration. The vendor’s infrastructure must align with your organization’s privacy policies.
Contracts should clearly define how the vendor can use your data, preventing unauthorized activities like marketing by setting strict purpose limitations. Also, confirm that their technology supports your workflows without creating vulnerabilities or requiring unsafe workarounds.
The Office of the Privacy Commissioner of Canada’s investigation into SWIFT highlighted that while contracts serve as the primary safeguard, they cannot override the legal and security requirements of the country where data is processed. This makes it essential to evaluate both the vendor’s technical setup and the legal environment in which they operate.
Plan regular reviews of the vendor’s infrastructure to ensure it continues to meet your privacy and security needs as they evolve.
Service Level Agreements and Support Terms
Your SLA should formalize key responsibilities, including breach notifications, incident reporting, and audit rights, to align with PIPEDA’s requirements. For instance, the SLA must specify breach notification timelines that allow you to meet PIPEDA’s "as soon as feasible" reporting standard. It should also require detailed incident reports that include encryption status and access details, enabling you to assess risks quickly.
Define uptime guarantees that match your operational needs, and clearly outline what constitutes "control" of personal information in the SLA. This ensures the vendor fully understands their compliance obligations. Additionally, audit rights should include access to the vendor’s incident logs, as the Privacy Commissioner may request these records to verify compliance.
Position the vendor as a collaborative partner in meeting these obligations, rather than merely a service provider. This ensures accountability and sets the stage for a reliable long-term relationship.
Planning Your Migration
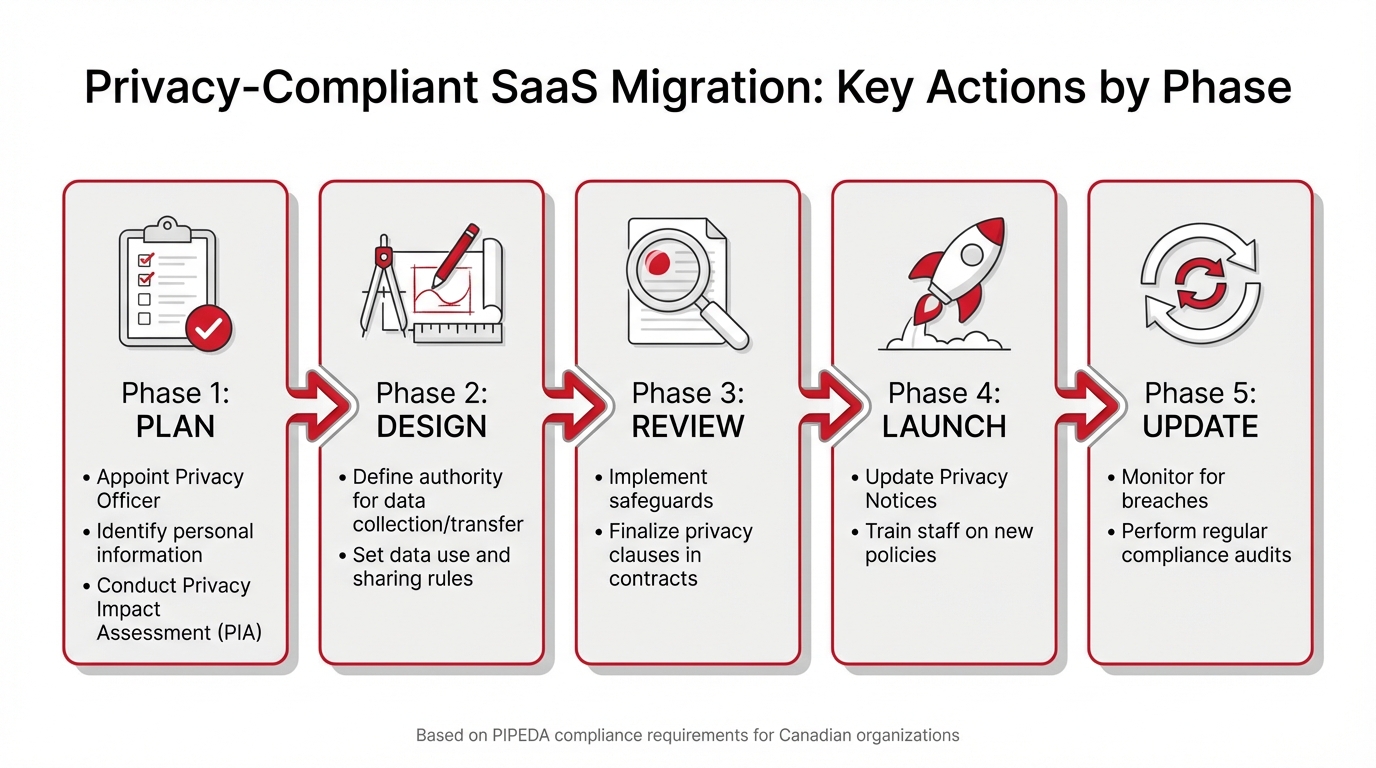
Privacy Impact Assessment Migration Phases for Canadian SaaS Helpdesk Compliance
Once your vendor’s compliance and security validation is confirmed, it’s time to plan your migration in well-defined phases. Start by assigning a Privacy Officer to oversee the process. Conduct a Privacy Impact Assessment (PIA) to identify potential risks, sort through your current data to distinguish what’s necessary from what’s not, and document the specific purposes for migrating the data.
Make sure your vendor contract includes privacy protection clauses that align with Canadian law and provide the right to audit. Keep in mind that data stored in a foreign country is still subject to that nation’s legal authority.
"An organization is responsible for personal information in its possession or custody, including information that has been transferred to a third party for processing. The organization shall use contractual or other means to provide a comparable level of protection while the information is being processed by a third party." – Principle 1, PIPEDA
Update your transparency practices by informing customers that their data may be processed in another country and could be accessed by that country’s law enforcement. Revise both your internal privacy manuals and public-facing materials – such as your website, brochures, and support documentation – to reflect these changes in your service provider and data storage locations.
Once these foundational steps are in place, turn your attention to building and preparing your migration team.
Before You Start the Migration
Gather a cross-functional team that includes end users, such as members of your support staff. Develop detailed runbooks that outline tasks, timelines, roles, and rollback plans. Conduct a pre-migration audit to establish baseline metrics. Address skill gaps early by involving support agents in the planning phase. This not only helps them feel included but also ensures their concerns are addressed. Set aside 10% to 15% of your project budget specifically for change management training. Use your audit to measure ticket volumes, response times, and resolution rates, which will help you identify whether any performance issues after migration are linked to the new platform or are just operational variances.
Running Tests and Pilot Programs
Once your team is ready, validate your migration plan through targeted tests and pilot programs. Start with non-critical applications or a small group of support staff to test the processes before a full-scale rollout. During this pilot phase, ensure that key PIPEDA compliance features are functioning as intended. For example, confirm that the helpdesk can differentiate between essential data collection and secondary purposes, giving users the option to opt out of non-essential uses. Test the system’s ability to handle individual access requests, ensuring your team can meet PIPEDA standards for accuracy and transparency. If possible, run the new helpdesk alongside your legacy system to compare outputs and verify data consistency. This step is crucial because data integrity issues can undermine user confidence. Use the pilot to simulate breach responses, testing your team’s ability to detect and report incidents quickly.
Preparing Your Team for the Change
Train both frontline staff and management to explain the updated privacy practices, address customer questions about foreign data processing, and handle access requests. It’s equally important to help users adapt to the new system. Highlight the practical benefits – like faster performance, better collaboration tools, and easier access to customer history – so your team understands how the platform improves their work. Plan for extra support during the initial post-migration phase, and monitor ticket volumes closely to identify areas where additional training or system tweaks might be needed. Finally, update your IT and support procedures to align with the new cloud-based workflows for user provisioning, access management, and system administration.
To tie it all together, here’s a summary of the key privacy actions at each phase of your migration:
| Migration Phase | Key Privacy Actions |
|---|---|
| Plan | Appoint Privacy Officer; Identify personal information; Conduct Privacy Impact Assessment |
| Design | Define authority for data collection/transfer; Set data use and sharing rules |
| Review | Implement safeguards; Finalize privacy clauses in contracts |
| Launch | Update Privacy Notices; Train staff on new policies |
| Update | Monitor for breaches; Perform regular compliance audits |
Conclusion
For Canadian teams considering a switch to a non-US SaaS helpdesk, it’s essential to carefully weigh legal, operational, and technical priorities. Remember, even when personal information is handled by a third-party processor, your organization remains accountable for its protection. To meet PIPEDA standards, ensure the vendor provides comparable safeguards through strong contractual agreements. These contracts should specify security measures, staff training, audit rights, and breach reporting requirements.
Additionally, transparency is key. Clearly inform customers that their data may be processed in another country and could be subject to foreign law enforcement access. This openness helps build trust and prepares the groundwork for addressing technical hurdles.
On the technical side, readiness is critical to a successful migration. Studies show that about 83% of cloud migrations encounter significant issues due to simple oversights, and 58% of decision-makers highlight skill gaps as a major obstacle. To avoid these pitfalls, use discovery tools for at least a month before starting the migration, conduct privacy impact assessments, and thoroughly test the new system in a non-production environment. These steps ensure data accuracy and compliance with PIPEDA.
Finally, appoint a senior privacy officer to oversee the process, establish clear audit procedures, and keep your team well-trained. They should not only understand the new platform’s features but also be prepared to explain updated privacy practices to customers. Proper preparation on all fronts will make the transition smoother and more secure.
FAQs
What data residency rules must Canadian public sector organizations follow?
Canadian public sector organizations must store personal data within the country’s borders. In most cases, transferring this data outside Canada is prohibited unless specific legal conditions are satisfied. These regulations aim to uphold Canada’s privacy and sovereignty standards.
When choosing SaaS providers, it’s crucial to verify whether they can meet data residency requirements and ensure their infrastructure complies with Canadian laws. This is especially important for entities managing sensitive or classified data.
What should Canadian companies consider to comply with privacy laws when using a non-US SaaS provider?
Canadian businesses can meet privacy law requirements by adhering to the principles outlined in PIPEDA and relevant provincial regulations. This involves taking steps like conducting privacy impact assessments to identify potential risks, ensuring SaaS providers have robust security protocols, and being upfront with users about where their data is stored and who might have access to it.
It’s also important for organizations to evaluate the legal framework in the provider’s country, include contractual terms that uphold Canadian privacy standards, and clearly inform users about the possibility of foreign access to their data. These measures are essential for safeguarding personal information and staying compliant with Canadian privacy laws when dealing with cross-border data.
What should a SaaS contract include to comply with PIPEDA requirements?
To align with PIPEDA regulations, your SaaS contract should clearly outline provisions for data protection, transparency, and accountability. This means detailing how personal information will be safeguarded, including the implementation of proper security measures. Additionally, the contract should confirm that data will only be processed for its intended purposes and with the necessary consent.
It’s also crucial to address data residency and cross-border transfers. The contract should specify that personal data will remain protected, no matter where it’s stored or processed. If data may be handled outside of Canada, individuals must be informed that it could be subject to the laws of those jurisdictions.
Include clauses covering breach notifications, audit rights, and ongoing compliance checks to ensure accountability and maintain trust. By addressing these elements, your organization can better adhere to PIPEDA’s guidelines while safeguarding personal information.










